Jottings
Mathematical reasoning may be regarded rather schematically as the exercise of a combination of two facilities, which we may call intuition and ingenuity. -Alan M. Turing
Here are some resources related to cryptography and mathematics that I found useful.
Cryptography
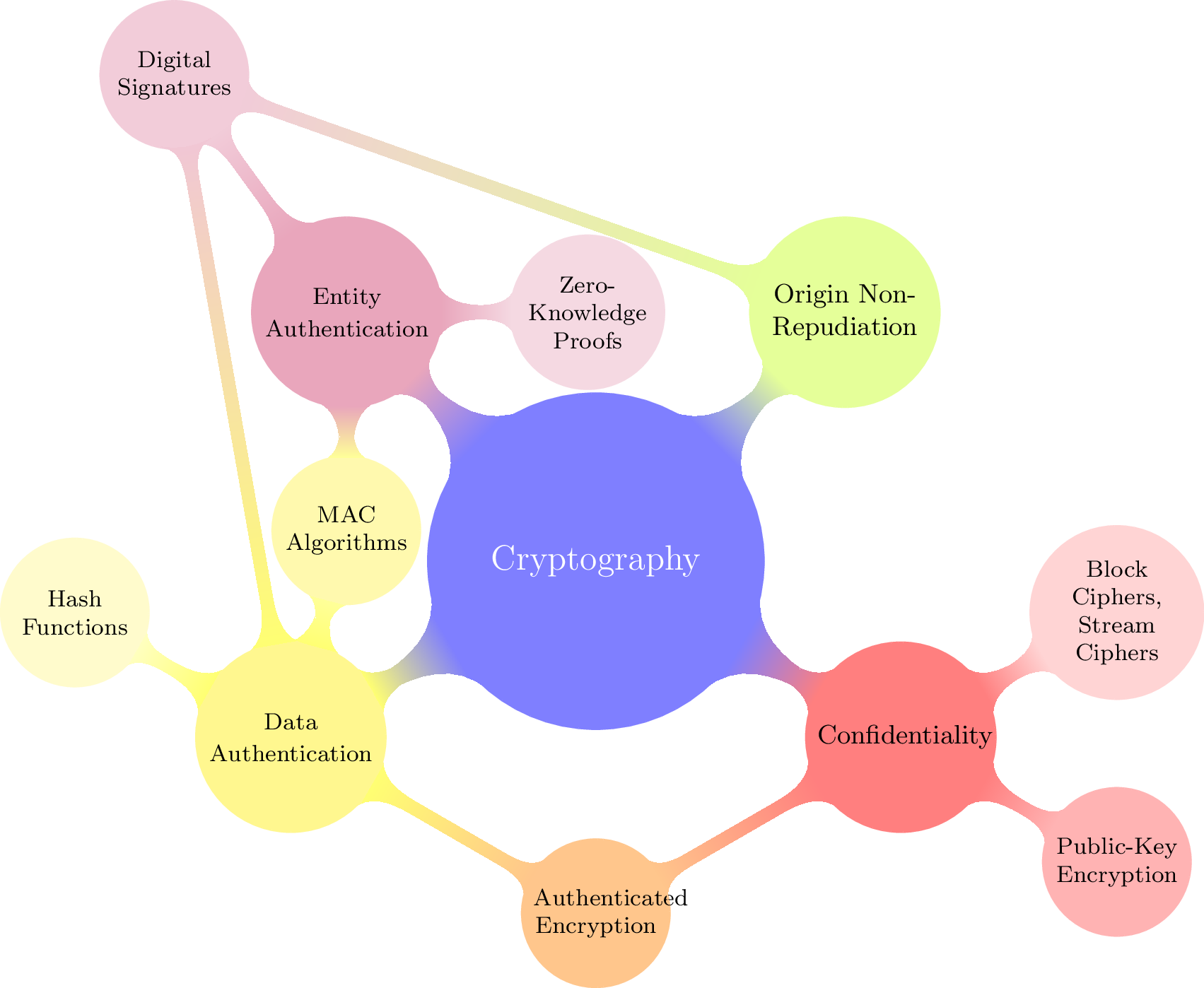
To get started, one can consider the following resources:
Computationally secure cryptography

These cryptosystems are considered secure against the computation power offered by humans with pencil-paper, computers, and quantum computers.
Pencil-paper safe cryptography
Classical computer safe cryptography
Quantum computer safe cryptography
Unconditionally secure cryptography

TODO: Quantum cryptography
Math tech
The following is a list of various math tech setups I have worked with over the years.
| Interval (years) | Operating system (user interface) | Primary software |
|---|---|---|
| 2013 to 2019 | Ubuntu (GNOME 2, LXDE, Unity, and Cinnamon) | TexMaker |
| 2019 to 2020 | Debian (Crostini/Linux on ChromeOS) | TexMaker |
| 2020 to 2021 | Fedora (Xfce and GNOME 3) | Vim+MuPDF |
| 2021 to 2023 | openSUSE (KDE Plasma 5) | Vim+MuPDF |
| 2023 to 2025 | Ubuntu (Windows Subsystem for Linux 2) | VSCode with LaTeX Workshop Extension |
Git
Git is a version control system that was developed to manage Linux development. I use GitHub as the remote server for my git repositories. Here is a tutorial to get started: https://swcarpentry.github.io/git-novice/
Some other useful resources:
- Git Guides: https://github.com/git-guides
- Git Cheatsheets: https://training.github.com/
- GitHub for Mathematicians: https://g4m.code4math.org/g4m.html
Markdown
Markdown is a markup language that was developed to bridge the gap between raw text and HTML. One can learn the basics here: https://www.markdownguide.org/
There are different flavors that add various features:
- GitHub flavor (kramdown with support for math, flowchart, and footnote): https://docs.github.com/en/get-started/writing-on-github
- Zettlr flavor (+KaTeX): https://docs.zettlr.com/en/reference/markdown-basics/
- Quarto flavor (Pandoc Markdown): https://quarto.org/docs/authoring/markdown-basics.html
- Ghostwriter flavor (CommonMark et al.): https://ghostwriter.kde.org/documentation/
TeX
TeX is a typesetting system that was developed to meet the needs of mathematical and scientific typography. There are different flavors that can be created by combining an engine like pdfTeX or XeTeX or LuaTeX with a format like LaTeX or ConTeXt. Moreover, LaTeX offers lots of packages, for example one can choose between BibTeX and BibLaTeX for bibiliography management. I use LaTeX with pdfTeX engine to produce PDF articles, reports, and presentations. Here is a tutorial to get started: https://edbennett.github.io/latex-tutorial/
Further readings:
Julia
Julia is a modern programming language that was developed to combine readability, speed, and scalability in one tool. It readily adopts cool features from other languages like its amazing package manager Pkg inspired by Rust’s cargo. One can learn the basics from this tutorial: https://github.com/JuliaAcademy/JuliaProgrammingForNervousBeginners
If new to programming, consider solving some exercises from CodeAbby or Project Euler.
Some other useful resources:
| Documentation | Packages |
|---|---|
| Style guide | Pluto |
| Performance tips | Revise |
| Unicode input | Hecke |
| Math operators | Oscar |
| Cheatsheet | LaTeXStings |
| Floating point math | Flux |
